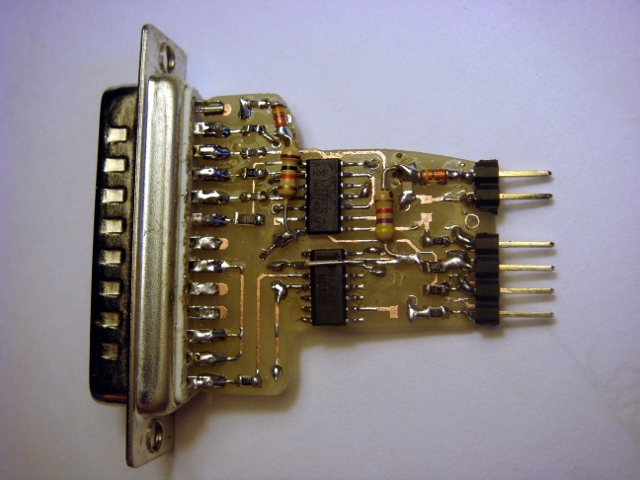
This Homemade Huawei Echolife BM622 4G WiMAX CPE broadband wireless modem router LAN LED programmer flasher is a DIY using LPT printer port on old legacy PC, beware of using USB to LPT it will not work.
The hardware schematic diagram is wide available on the net, likewise part can be also purchased at local store. You can download the Willem programmers its free, Programmer is very cost effective and suitable for electronic applications (PC BIOS, satellite receivers, DVD update/repair and more...).
Latest HW version EZoFlash4v5
EZoFlash+ 4v4
Schematic Diagram :
Programmer EZoFlash support :
- 8bit , 8/16bit and 16 bit flash memory in TSOP, PSOP, DIP and PLCC packages,
- EPROM, E(E)PROM and E2PROM parallel memory, FWH/LPC and AT89C51 family,
- +3.3V and +5.0V Vcc devices,
- address range to 64Mbit (..A22),
- +12V driver for programming and temporary sector unprotection,
- adapters with standard sockets for DIP and PLCC devices,
- adapters with memory chip soldering or surface mount identical footprint sockets (Meritec, Yamaichi) for TSOP , PSOP and SSOP devices,
- software commands - get ID, read, verify, erase, blank check and program.
- Latest version EZoFlash4v5 support serial EEPROM (I2C, Microwire, SPI), SPI Flash, Microchip PIC, Atmel AVR-8bit MCU (ATmega, ATtiny, AT90)
1.) Power supply output voltage +15…+18V, max current 300mA or more. Be sure , power supply connector internal positiv ! Recommended power supply with stabilised output voltage.
Check filtered non-stabilised power supply output voltage drop, load shortly power supply connector with resistor about 150 Ohm (load 100-120mA). Output voltage schould remain in recommended voltage range. Expect EPROM adapters use, check power supply voltage with resistor about 47 Ohm (load 300-350mA).
DC Power Jack and Plug are available with internal pin diameter 2.1mm or 2.5mm. Adapt both connectors for the same size.
Be sure on power supply isolated output voltage, no static voltage between power supply connector and computer grounds.
2.) Programmer EZoFlash+ default jumpers are Jp1, Jp3, Jp5.
Programmer logic IC and target chip have +5V voltage, A18 used on connector BU3.
Change jumper Jp5 (A18) to Jp4 (RST/Vpp) for BU3 based adapters only where Vpp or RST required , read settings in adapters page.
Change jumpers Jp1, Jp3 (+5V) to Jp2 (programmer +4.3V, target chip +3.6V) for low voltage (2.7-3.6V) target memory chip.
Change jumpers Jp1, Jp3 (+5V) to Jp2, Jp3 (+4.3V) for FWH/LPC adapters.
Other voltage options are available, for example all jumpers Jp1..Jp3 removed – programmer +3.6V, target chip +2.95V.
3.) Required adapter for target chip find in EZoFlash adapters page. Details and settings find on selected adapter page.
Corresponding flash memory and FWH/LPC chip adapter can be found in chip database.
Common jumpers on adapters – Jp7 (Vpp=Vcc), Jp8 (Vpp=+12V)
Extra adapter – voltage converter dc2dc_a4 is used with EPROM adapters to have higher programming voltages (Vcc=+5.7V , +6.2V ; Vpp= +12.5V…+13.2V, +21V, +25V)
Crossadapter prot_a1 is used for 8-bit flash memory adapters to provide sector lock/unlock in high voltage autoselect mode.
Verified chips, used adapters and test results are summarized in chip_test file.
4.) EZoFlash+ programmer works with Willem group programmer software in main PC OS , Windows XP and Windows 98SE preferably. Recommended latest software version 0.97ja. Sometimes useful are old versions 0.97g and 0.94a .
Software versions 0.98b, 0.98c, 0.98dx (0.98d2,.. 0.98d5) are not EZoFlash+ compatible.
Have a file setup97ja.exe, run it and follow to guide. Directory EPROM3 with files EpromM51.exe and io.dll will be created in Program Files. Uninstall option , Shortcuts in Desktop and Programs Menu are available.
Have a package with files EpromM51.exe (10.06.2004, 0.97ja ) and io.dll, unzip it and place both files in the same directory.
Have a package with files EpromM51.exe (26.01.2003, 0.97g or 21.02.2004, 0.94a) , dlportio.sys, dlportio.dll , unzip it and place all files in the same directory.
Click on program icon or it shortcut, programmer software window is launched.
5.) Utility 29C0x0.exe read boot block lockout on Atmel and Winbond small sector flash memory. Winbond chips boot block lockout can be enabled/disabled.
Utility hvasm.exe allow 8 bit flash memory sector lock/unlock in high voltage autoselect mode.
6.) Printer LPT extension cable is used to connect programmer and PC. Cable has 2 connectors (male and female), wired 1:1 according pin numbers. Shorter cable is recommended, but no more than 1.8m. Cable wires should be shielded , shield connected to both connectors housing. Long cable, bad quality and without shield may cause random errors in data transfer.
7.) Willem software supports programmer connected to standard LPT1, LPT2 or LPT3 port. Set selected in programmer software, settings “Printer Port”
Laptops with parallel port converters, PC with specific LPT port adress are not supported.
Recommended install registry XP_stop_polling.reg on PC with Windows XP. It stops PC internal resources random access/scan to LPT port. Check and close active resident programs that can use parallel port.
Generally data transfer works on default LPT port settings. Check parallel port settings in PC BIOS, sometimes change from ECP mode to EPP or Normal required.
Utilities are LPT1 supported only.
8.) Installing sequence.
- Connect LPT cable to PC and programmer.
- Run Willem software.
- Connect power supply to programmer. Programmer green LED flash only.
- Run Willem SW command Help/Test Hardware. Expect reply “Hardware present”
- Insert adapter with target memory chip.
- Run Read/Erase/Blank check/Program.
- Command in progress – red LED flash (Vcc on), yellow LED flash (Vpp on).
- Command finished, programmer green LED flash only. Remove adapter or replace target memory chip.
9.) Powered programmer - don’t connect and disconnect LPT cable.
Software not launched - don’t use or install adapter with target memory chip. All LED’s can flash on powered and connected programmer without software, target chip can be damaged !!
Command in progress, red or yellow LED flash - don’t remove or install adapter with target memory chip.
10.) Share your experience and problems in EZoFlash forum.